Numerous malware threats and scares over the past few months, and it is now pretty much established that Android devices face greater security risks. These risks are compounded by the existence of many stakeholders who are often not on the same page as Google when it comes to phone’s software. Majority of the phone makers like to tinker with the original Android and customise it to add features that would help them distinguish their smartphones from their rivals within the ecosystem.
They often overlook Google’s updates and try to compensate for it with their own firmware updates. With time even these updates dry up and the users are left to fend for themselves or switch to a new smartphone that runs a newer version of the Android OS.
As per Google’s statistics released on 11 January, 2017, about 33℅ of Android phones are still running a three year old Lollipop version of Android is, while 22.6℅ are still based on an even older Android KitKat OS. The latest Nougat is available on just 0.7℅ of smartphones yet.
Security risk caused by lax attitude of phone makers
Providing regular security patches through OTA updates is the only way old Android phones can be readied to combat new generation malwares. Most OEMs provide these updates only on their latest or flagship smartphones.
After the notorious Stagefright malware was reported by anti-virus company Zimperium in 2015, Google found a fix and released a security patch on its Nexus smartphones and those made by other OEMs. While the likes of LG, OnePlus, Samsung and Lenovo were quick to pass it on to users not many OEMs showed the same alacrity.
The heavy competition between Android phonemakers sees them launch multiple devices within short time periods. Keeping tab of software updates for all the devices running on different configuration and hardware becomes more difficult, and the ones that are not so new anymore, are ignored.
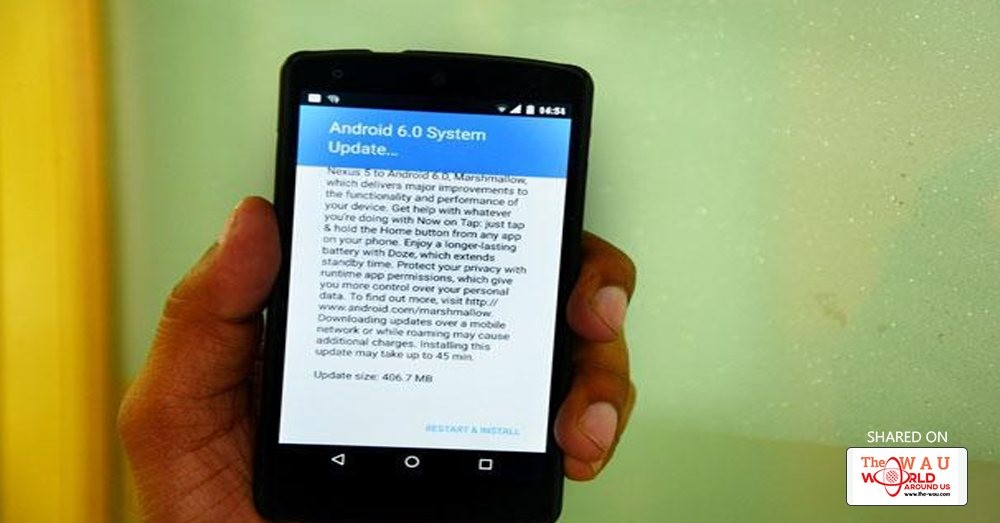
Features such as app permissions that can help users identify which apps are actually snooping on them and stop them from doing so was made available to user on Android 6.0 (Marshmallow). Barring a few devices with custom UIs, users on old Android OS still don’t have access to these features.
How customization in itself has risks?
A study published in 2014 by scientists from University of Illinois and Indiana University found that software customisation made by OEMs puts Android devices at greater risk. After Google makes Android OS available to OEMs, these OEMs make changes to add their apps, device drivers and their trademark features. The study point out that Android is a multi-layered system where the app layer and framework layer sits at the top of a set of C libraries and Linux kernel. Device drivers work on the layer with Linux kernel and are closely integrated to framework services such as Location Service and Media Service. if the customisation overlooks any of these integrations can leave the overall device vulnerable. In the absence of timely software updates and security patches, such phones can be exploited by hackers.
Different approach to encryption
A security tool available on Android smartphones is full device encryption. It showed up first on Android 2.3 (Gingerbread), but became a permanent fixture from Android 5.0 onwards. While some OEMs such as Blackberry provide full device encryption out of the box in many cases users have to do it manually in the phone’s settings.
While it adds a layer of security, it is not entirely secure as the full device encryption on Apple’s iOS. The major difference lies in the way the encryption is implemented.
Every iOS device generates a 256-bit unique identification number which is integrated with the hardware right from the beginning. Thus not only binds it to the device but also makes it unmodifiable. This key cannot be accessed through the software which makes the data on the phone bounds for every one except the owner of the device.
In case of Android, the full device encryption is built on software and not on the hardware, which means the encryption keys are saved on the software. It is this loophole which can be exploited to gain access to an encrypted device. While it is not full-proof, full device encryption provides some level of security, but you need a phone running Android 5.1 or higher to take advantage of it.
Pre-loaded tools
Many phone makers take pride in the security tools they offer with their custom Android UI from the start itself. Pre-loaded anti-virus tools which run regular scans and keep an eye on user’s web activities to protect them against any vulnerabilities is very common these days. These tools can only tell if your device is at risk, and may not be able to protect your data.
Share This Post